BLE Hacking:使用Ubertooth one扫描嗅探低功耗蓝牙
本文作者:雪碧0xroot@漏洞盒子安全实验室
0×00 前言
低功耗蓝牙(Low Energy; LE),又视为Bluetooth Smart或蓝牙核心规格4.0版本。其特点具备节能、便于采用,是蓝牙技术专为物联网(Internet of Things; IOT)开发的技术版本。
类似文章推荐: 永不消逝的电波(三):低功耗蓝牙(BLE)入门之如何调戏别人的小米手环 。
BLE主打功能是快速搜索,快速连接,超低功耗保持连接和传输数据,弱点是数据传输速率低,由于BLE的低功耗特点,因此普遍用于穿戴设备。
我们比较熟悉的网络有 Zigbee,WIFI、Bluetooth(传统蓝牙),三者之间的关系如下:
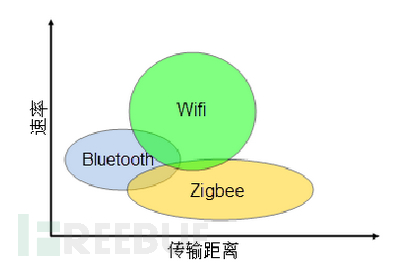
不同的无线数据传输协议在数据传输速率利传输距离有各自的使用范围。Zigbee、蓝牙以及 WIFI 标准都是工作在 2.4GHz 频段的无线通信标准。
传统蓝牙数据传输速率小于 3Mbps,典型数据传输距离为 2-10m,蓝牙技术的典型应用是在两部手机之间进行小量数据的传输。
WIFI 最高数据传输速率可达 50Mbps,典型数据传输距离在 30-100m,WIFI 技术提供了一种 Intemet 的无线接入技术。
0×01 蓝牙与低功耗蓝牙
1.1 标准
蓝牙无线技术是使用范围最广泛的全球短距离无线标准之一,全新的蓝牙 4.0 版本将传统蓝牙,高速蓝牙和低功耗蓝牙技术三种蓝牙技术合而为一。它集成了蓝牙技术在无线连接上的固有优势,同时增加了高速蓝牙和低功耗蓝牙的特点,这三个规格可以组合使用,也可以单独使用,低功耗蓝牙即 ble 是蓝牙 4.0 的核心规范,该技术最大特点是拥有超低的运行功耗和待机功耗,蓝牙低功耗设备使用一粒纽扣电池可以连续工作数年之久,可应用与对成本和功耗都有严格要求的无线方案,而且随之智能机的发展将有着更加广泛的领域。
BLE分为三部分Service、Characteristic、Descriptor,这三部分都由UUID作为唯一标示符。一个蓝牙4.0的终端可以包含多个Service,一个Service可以包含多个Characteristic,一个Characteristic包含一个Value和多个Descriptor,一个Descriptor包含一个Value。
BLE 规范中定义了 GAP(Generic Access Profile)和 GATT(Generic Attribute)两个基本配置文件。
GAP 层 负责设备访问模式和进程,包括设备发现,建立连接,终止连接。初始化安全特征和设备配置。
GATT 层 用于已连接的蓝牙设备之间的数据通信。
1.2 BLE特点&优势
1.2.1高可靠性
对于无线通信而言,由于电磁波在传输过程中容易受很多因素的干扰,例如,障碍物的阻挡、天气状况等,因此,无线通信系统在数据传输过程中具有内在的不可靠性。蓝牙技术联盟 SIG 在指定蓝牙 4.0 规范时已经考虑到了这种数据传输过程中的内在的不确定性,在射频,基带协议,链路管理协议中采用可靠性措施,包括:差错检测和矫正,进行数据编解码,数据降噪等,极大地提高了蓝牙无线数据传输的可靠性,另外,使用自适应调频技术,能最大程度地减少和其他 2.4G 无线电波的串扰。
1.2.2 低成本、低功耗
低功耗蓝牙支持两种部署方式:双模式和单模式,一般智能机上采用双模式,外设一般采用 BLE 单模。
BLE 技术可以应用于 8-bit MCU, 目前 TI 公司推出的兼容 BluetoothLE 协议的 SoC芯片 CC254X 每片价格在 7.6 元左右, 外接几个阻容器件构成的滤波电路和 PCB 天线即可实现网络节点的构建。Nodic的NRF51822也不过才10元人民币。
低功耗设计:蓝牙 4.0 版本强化了蓝牙在数据传输上的低功耗性能,功耗较传统蓝牙降低了 90%。
传统蓝牙 设备的待机耗电量一直是其缺陷之一,这与传统蓝牙技术采用16至32个频道进行广播有很大关系,而低功耗蓝牙仅适用 3个广播通道,且每次广播时射频的开启时间也有传统的 22.5ms 减少到 0.6~1.2ms,这两个协议规范的改变,大幅降低了因为广播数据导致的待机功耗。
低功耗蓝牙 设计用深度睡眠状态来替换传统蓝牙的空闲状态,在深度睡眠状态下,主机 Host 长时间处于超低的负载循环 Duty Cycle 状态,只在需要运作时由控制器来启动,由于主机较控制器消耗的能源更多,因此这样的设计也节省了更多的能源。
1.2.3 快速启动、瞬间连接
此前蓝牙版本的启动速度非常缓慢,2.1 版本的蓝牙启动连接需要 6s 时间,而蓝牙4.0 版本仅需要 3ms 即可完成,几乎是瞬间连接。
1.2.4 传输距离极大提供
传统蓝牙传输距离一般 2-10m,而蓝牙 4.0 的有效传输距离可以达到 60~100m,传输距离提升了 10 倍,极大开拓了蓝牙技术的应用前景。
1.2.5 高安全性
为了保证数据传输的安全性,使用 AES-128 CCM 加密算法进行数据包加密认证,对于初学阶段,安全性问题可以暂时不考虑。
1.3 协议栈
协议栈内容请参考: Understanding Bluetooth Advertising Packets 一文。
中文版: http://blog.csdn.net/ooakk/article/details/7302425
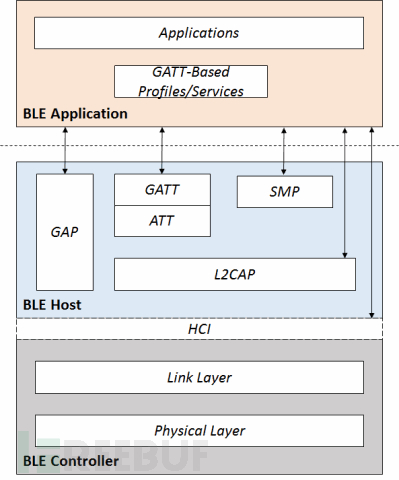
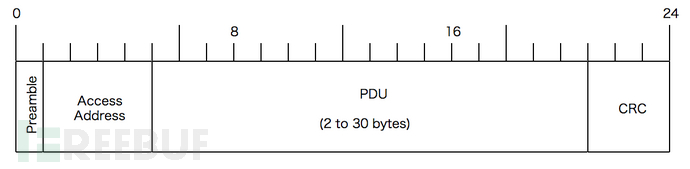
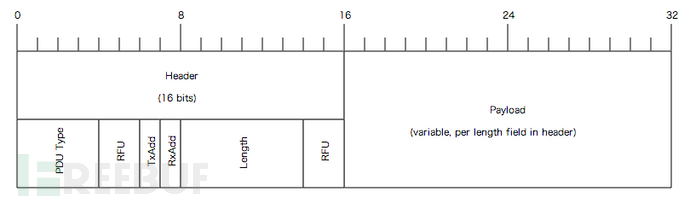
1.4 通信信道
BLE 工作在 ISM 频带,定义了两个频段,2.4GHz 频段和 896/915MHz 频带。在IEEE802.15.4 中共规定了 27 个信道:
在 2.4GHz 频段,共有 16 个信道,信道通信速率为 250kbps:
在 915MHz 频段,共有 10 个信道,信道通信速率为 40kbps:
在 868MHz 频段,有 1 个信道,信道通信速率为 20kbpS。
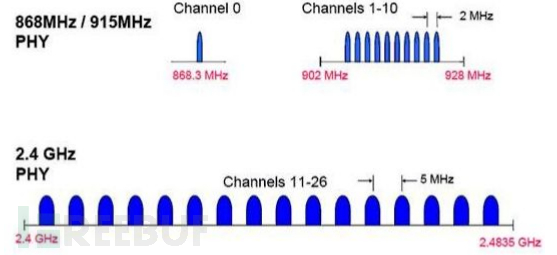
BLE 工作在 2.4GHz 频段,仅适用 3 个广播通道,适用所有蓝牙规范版本通用的自适应调频技术。
BlueTooth 有79个射频信道,按0-78排序,并于2402 MHz开始,以1 MHz分隔:
channel 00 : 2.402000000 Ghz channel 01 : 2.403000000 Ghz … channel 78 : 2.480000000 Ghz BTLE有40个频道(也称为信道),按37在第一个,后面由0-36,然后第39信道(那么38呢  )第38信道位于10和11之间:
)第38信道位于10和11之间:
channel 37 : 2.402000000 Ghz channel 00 : 2.404000000 Ghz channel 01 : 2.406000000 Ghz channel 02 : 2.408000000 Ghz channel 03 : 2.410000000 Ghz channel 04 : 2.412000000 Ghz channel 05 : 2.414000000 Ghz channel 06 : 2.416000000 Ghz channel 07 : 2.418000000 Ghz channel 08 : 2.420000000 Ghz channel 09 : 2.422000000 Ghz channel 10 : 2.424000000 Ghz channel 38 : 2.426000000 Ghz channel 11 : 2.428000000 Ghz channel 12 : 2.430000000 Ghz channel 13 : 2.432000000 Ghz channel 14 : 2.434000000 Ghz channel 15 : 2.436000000 Ghz channel 16 : 2.438000000 Ghz channel 17 : 2.440000000 Ghz channel 18 : 2.442000000 Ghz channel 19 : 2.444000000 Ghz channel 20 : 2.446000000 Ghz channel 21 : 2.448000000 Ghz channel 22 : 2.450000000 Ghz channel 23 : 2.452000000 Ghz channel 24 : 2.454000000 Ghz channel 25 : 2.456000000 Ghz channel 26 : 2.458000000 Ghz channel 27 : 2.460000000 Ghz channel 28 : 2.462000000 Ghz channel 29 : 2.464000000 Ghz channel 30 : 2.466000000 Ghz channel 31 : 2.468000000 Ghz channel 32 : 2.470000000 Ghz channel 33 : 2.472000000 Ghz channel 34 : 2.474000000 Ghz channel 35 : 2.476000000 Ghz channel 36 : 2.478000000 Ghz channel 39 : 2.480000000 Ghz40个频道中:37、38、39为广播信道,另外37个频道用于数据的传输:
使用德州仪器(TI)CC2540蓝牙低功耗模块配合官方的SmartRF协议软件包监听器:PACKET-SNIFFER,可对三个蓝牙广播信道进行嗅探。

使用方法可参考: Ti.com.cn/packet-sniffer 这种嗅探方案优点是廉价,不足是只能嗅探到广播信道的数据包,无法捕获连接完成后也就是设备通信过程中的数据包:
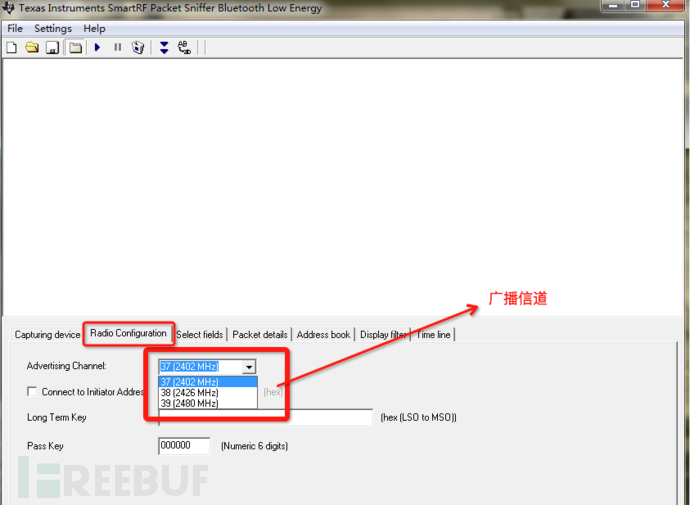
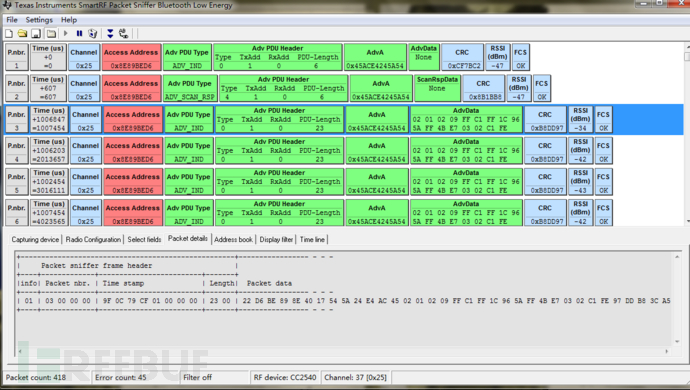
基于HackRF嗅探蓝牙数据包实际上也是可行的:
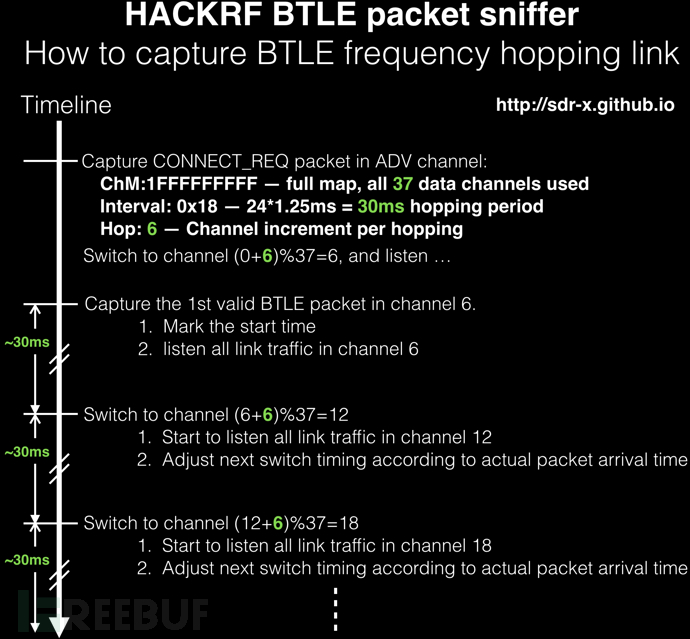
其方法参考jxj童鞋的 BTLE packet sniffer based on HACKRF (function and performance similar to TI’s packet sniffer)
HackRF.NET 中文版: 基于HACKRF的低功耗蓝牙(BTLE)packet sniffer/scanner
0×02 环境搭建:
我们说到上面的方案只能嗅探到广播信道的数据包,无法捕获通信过程中的蓝牙数据包,接下来我们将使用Ubertooth One来弥补上面方案的缺陷。
2.1安装lib库
apt-get install python-software-properties add-apt-repository ppa:pyside apt-get update apt-get install libnl-dev libusb-1.0-0-dev pyside-tools2.2 安装libbtbb
wget https://github.com/greatscottgadgets/libbtbb/archive/2015-09-R2.tar.gz -O libbtbb-2015-09-R2.tar.gz tar xf libbtbb-2015-09-R2.tar.gz cd libbtbb-2015-09-R2 mkdir build cd build cmake .. make sudo make install
2.3 安装ubertooth
wget https://github.com/greatscottgadgets/ubertooth/releases/download/2015-09-R2/ubertooth-2015-09-R2.tar.xz -O ubertooth-2015-09-R2.tar.xz tar xf ubertooth-2015-09-R2.tar.xz cd ubertooth-2015-09-R2/host mkdir build cd build cmake .. make sudo make install sudo ldconfig
2.4 安装wireshark
sudo apt-get install checkinstall
wget https://www.wireshark.org/download/src/wireshark-2.0.3.tar.bz2
tar -xvf wireshark-2.0.3.tar.bz2
cd wireshark-2.0.3
./configure
make
make install
2.5 安装kismet
wget https://kismetwireless.net/code/kismet-2013-03-R1b.tar.xz tar xf kismet-2013-03-R1b.tar.xz cd kismet-2013-03-R1b ln -s ../ubertooth-2015-09-R2/host/kismet/plugin-ubertooth . ./configure make && make plugins sudo make suidinstall sudo make plugins-install2.6 安装BLE解密工具crackle ( 开源项目地址 )
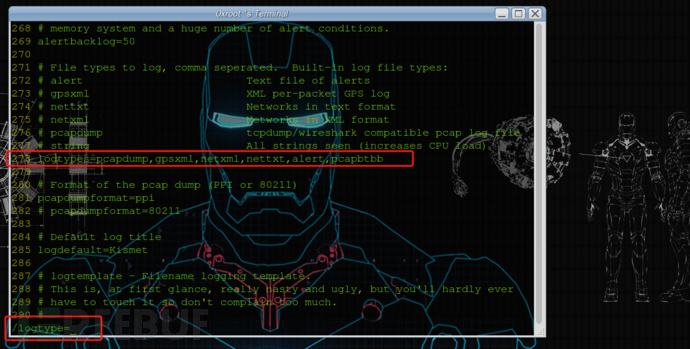
git clone https://github.com/mikeryan/crackle.git cd crackle make make install找到kismet的配置文件kismet.conf ,把”pcapbtbb”加入到kismet.conf的logtypes= 里边

0×03 嗅探扫描
3.1 spectool
spectool_curses

spectool_gtk 扫描附近信号并在频谱上显示:

spectool_raw RAW中文解释是“原材料”或“未经处理的东西”,这里猜测是显示设备捕获到的未经处理的信号数据:
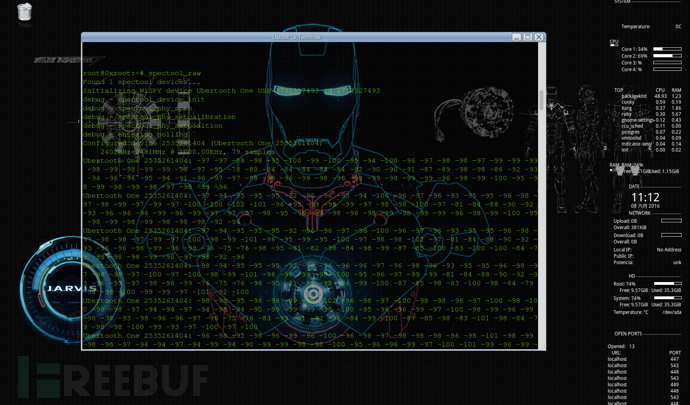
spectool_net 显示设备监听TCP/IP端口
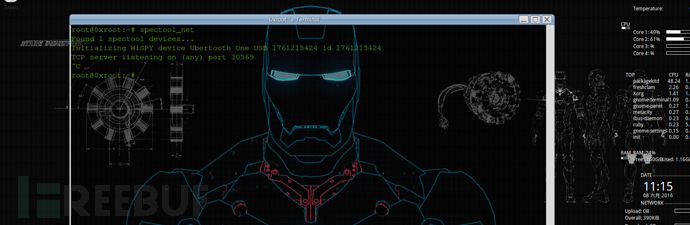
3.2 hcitool
root@0xroot:~# hcitool --help hcitool - HCI Tool ver 4.99 Usage: hcitool [options] <command> [command parameters] Options: --help Display help -i dev HCI device Commands: dev Display local devices inq Inquire remote devices scan Scan for remote devices name Get name from remote device info Get information from remote device spinq Start periodic inquiry epinq Exit periodic inquiry cmd Submit arbitrary HCI commands con Display active connections cc Create connection to remote device dc Disconnect from remote device sr Switch master/slave role cpt Change connection packet type rssi Display connection RSSI lq Display link quality tpl Display transmit power level afh Display AFH channel map lp Set/display link policy settings lst Set/display link supervision timeout auth Request authentication enc Set connection encryption key Change connection link key clkoff Read clock offset clock Read local or remote clock lescan Start LE scan lewladd Add device to LE White List lewlrm Remove device from LE White List lewlsz Read size of LE White List lewlclr Clear LE White list lecc Create a LE Connection ledc Disconnect a LE Connection lecup LE Connection Update
hcitool scan : 扫描附近蓝牙设备
hcitool lescan : 扫描附近低功耗蓝牙设备
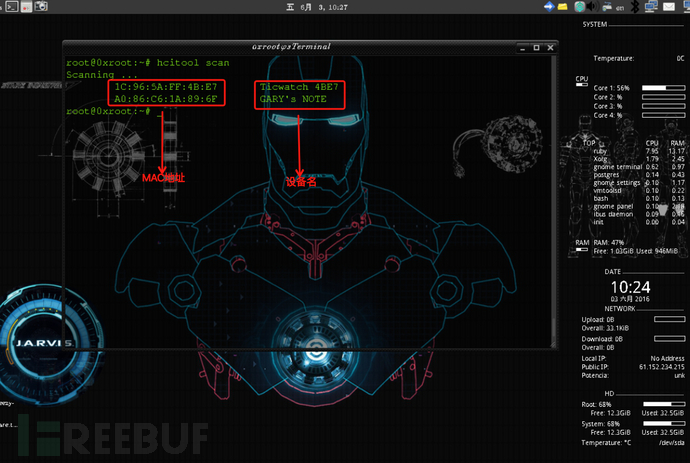
3.3 gatttool
root@0xroot:~# gatttool -h Usage: gatttool [OPTION...] Help Options: -h, --help Show help options --help-all Show all help options --help-gatt Show all GATT commands --help-params Show all Primary Services/Characteristics arguments --help-char-read-write Show all Characteristics Value/Descriptor Read/Write arguments Application Options: -i, --adapter=hciX Specify local adapter interface -b, --device=MAC Specify remote Bluetooth address -m, --mtu=MTU Specify the MTU size -p, --psm=PSM Specify the PSM for GATT/ATT over BR/EDR -l, --sec-level=[low | medium | high] Set security level. Default: low -I, --interactive Use interactive mode
gatttool -b 1C:96:5A:FF:4B:E7 -I [ ][1C:96:5A:FF:4B:E7][LE]> help help Show this help exit Exit interactive mode quit Exit interactive mode connect [address] Connect to a remote device disconnect Disconnect from a remote device primary [UUID] Primary Service Discovery characteristics [start hnd [end hnd [UUID]]] Characteristics Discovery char-desc [start hnd] [end hnd] Characteristics Descriptor Discovery char-read-hnd <handle> [offset] Characteristics Value/Descriptor Read by handle char-read-uuid <UUID> [start hnd] [end hnd] Characteristics Value/Descriptor Read by UUID char-write-req <handle> <new value> Characteristic Value Write (Write Request) char-write-cmd <handle> <new value> Characteristic Value Write (No response) sec-level [low | medium | high] Set security level. Default: low mtu <value> Exchange MTU for GATT/ATT [ ][1C:96:5A:FF:4B:E7][LE]> 3.4 ubertooth-scan
root@0xroot:~# ubertooth-scan --help ubertooth-scan: invalid option -- '-' ubertooth-scan - active(bluez) device scan and inquiry supported by Ubertooth Usage: -h this Help -U<0-7> set ubertooth device to use -s hci Scan - perform HCI scan -t scan Time (seconds) - length of time to sniff packets. [Default: 20s] -x eXtended scan - retrieve additional information about target devices -b Bluetooth device (hci0)
ubertooth-scan -s
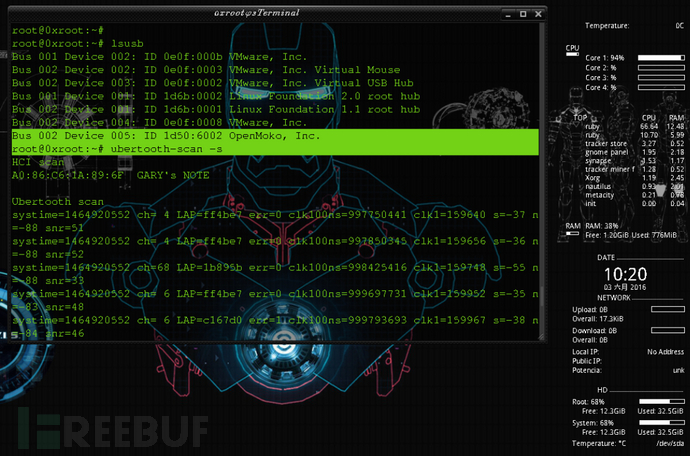
3.5 ubertooth-btle
ubertooth-btle - passive Bluetooth Low Energy monitoring Usage: -h this help Major modes: -f follow connections -p promiscuous: sniff active connections -a[address] get/set access address (example: -a8e89bed6) -s<address> faux slave mode, using MAC addr (example: -s22:44:66:88:aa:cc) -t<address> set connection following target (example: -t22:44:66:88:aa:cc) Interference (use with -f or -p): -i interfere with one connection and return to idle -I interfere continuously Data source: -U<0-7> set ubertooth device to use Misc: -r<filename> capture packets to PCAPNG file -q<filename> capture packets to PCAP file (DLT_BLUETOOTH_LE_LL_WITH_PHDR) -c<filename> capture packets to PCAP file (DLT_PPI) -A<index> advertising channel index (default 37) -v[01] verify CRC mode, get status or enable/disable -x<n> allow n access address offenses (default 32) If an input file is not specified, an Ubertooth device is used for live capture. In get/set mode no capture occurs.
ubertooth-btle -f -c test.pcap 抓包 & 保存到本地
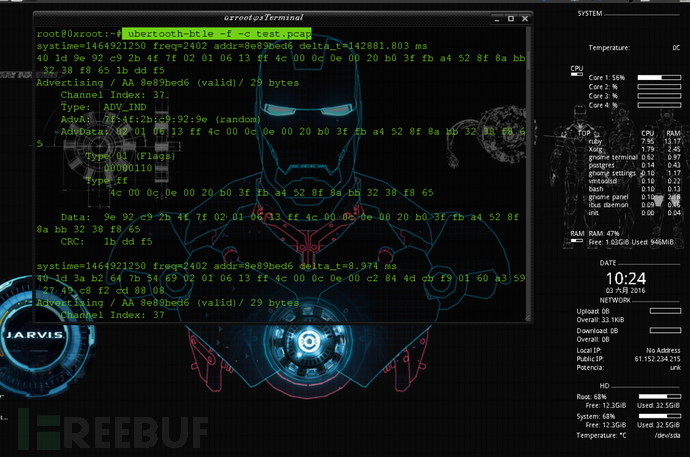
使用这条命令我们可以把设备捕获到的数据包保存到本地,完成后可导入wireshark进行数据包、协议分析。
wireshark导入嗅探到的蓝牙数据包需要处理一下才能正常查看,不然无法正常分析数据:

Edit → Preferences → Protocols → DLT_USER → Edit → New
在payload protocol中输入btle
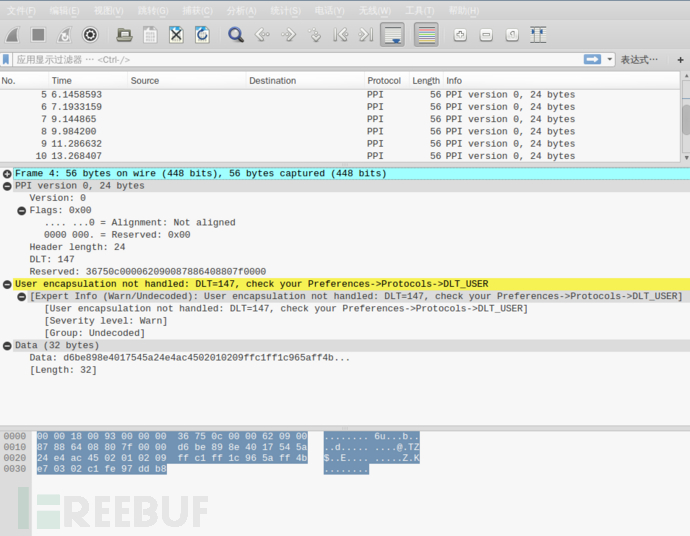

使用规则过滤数据包:参考 Capturing BLE in Wireshark
btle.data_header.length > 0 || btle.advertising_header.pdu_type == 0x05 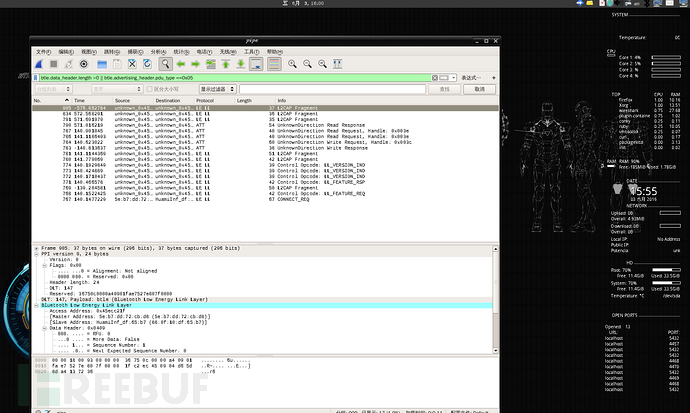
3.6 crackle
如果捕获到足够的数据包尤其是btsmp,那接下来便可以用crackle来破解tk和ltk:
crackle -i <file.pcap>解密数据包,并把解密后的包另存:
crackle -i <file.pcap> -o <output.pcap> crackle -i <file.pcap> -o <out.pcap> -l <ltk>
0×04 参考 && 感谢
Now I wanna sniff some Bluetooth: Sniffing and Cracking Bluetooth with the UbertoothOne
http://j2abro.blogspot.com.au/2014/06/understanding-bluetooth-advertising.html
路人甲@乌云drops:Bluetooth Low Energy 嗅探
疯狗@乌云drops:物联网安全拔“牙”实战——低功耗蓝牙(BLE)初探
http://j2abro.blogspot.com.au/2014/06/understanding-bluetooth-advertising.html
http://j2abro.blogspot.com.au/2014/06/analyzing-bluetooth-advertising-with.html
http://cerescontrols.com/tutorials-3/sniffing-bluetooth-packets-with-kismet-and-wireshark-in-ubuntu-12-04/
https://github.com/greatscottgadgets/ubertooth/wiki/Build-Guide
https://github.com/greatscottgadgets/ubertooth/wiki/Capturing-BLE-in-Wireshark
http://stackoverflow.com/questions/23877761/sniffing-logging-your-own-android-bluetooth-traffic
https://lacklustre.net/bluetooth/wireshark.html
https://blog.lacklustre.net/posts/BLE_Fun_With_Ubertooth:_Sniffing_Bluetooth_Smart_and_Cracking_Its_Crypto/
http://superuser.com/questions/947593/how-can-i-sniff-bluetooth-traffic-coming-from-my-and-another-device
http://www.backtrack-linux.org/forums/showthread.php?t=41552
http://www.splitbits.com/2014/05/14/ubertooth-spectools-chromebook/
http://ubertooth.sourceforge.net/usage/start/
http://hackerific.net/2012/01/28/Spectrum-Tools-and-Ubertooth-One/
https://penturalabs.wordpress.com/2014/02/20/ubertooth-updated-for-2014/
https://blog.lacklustre.net/
* 作者:雪碧0xroot@漏洞盒子安全实验室,转载请注明来自FreeBuf黑客与极客(FreeBuf.COM)
- 本文标签: App 软件 build 文章 ORM wget ip map 开源项目 智能 input file example python Service update remote 安全 漏洞 CTO Chrome Connection ACE 物联网 Ubuntu 端口 cat IDE TCP list 自适应 Word Security 云 cmd 进程 数据 时间 value Uber http 监听器 linux 认证 tar 黑客 GitHub key 开源 主机 Logging wordpress 协议 UI Android 开发 src kk root https 配置 SDN HTML 小米 lib 2015 plugin PHP git 安装 管理
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二











![[HBLOG]公众号](http://www.liuhaihua.cn/img/qrcode_gzh.jpg)

