OpenVZ VPS 额外支持
安装 Open VPN
这个是基于OpenVZ VPS,并不适合XEN VPS,XEN VPS请参考下面的架设 pptp 部分。开启 tun 支持
在 putty 里面运行如下命令,检查是否开启了tun设备:ls /dev/net/如果出现如下提示,表示已经开启,否则需要开启 tun 支持。
root@241541:/etc/openvpn# ls /dev/net/ tun注意开启 Tun 设备会导致 VPS 重启一次。如果有正在编辑的文档,请先退出。 登录到VPS的管理面板,点击右侧的 Info & Security 后,再点击 Enable Tun/Tap ,在随后的对话框点确定开启。

安装 openvpn
在 putty 里面运行如下命令安装 openvpn,再提示输入 (Y/n) 时,输入 Y 回车继续:apt-get install openvpn执行结果如下:
root@241541:~# apt-get install openvpn Reading package lists... Done Building dependency tree Reading state information... Done The following extra packages will be installed: liblzo2-2 libpkcs11-helper1 openvpn-blacklist Suggested packages: resolvconf The following NEW packages will be installed: liblzo2-2 libpkcs11-helper1 openvpn openvpn-blacklist 0 upgraded, 4 newly installed, 0 to remove and 53 not upgraded. Need to get 1601kB of archives. After this operation, 3760kB of additional disk space will be used. Do you want to continue [Y/n]? Get:1 http://archive.ubuntu.com/ubuntu/ maverick/main liblzo2-2 i386 2.03-2 [63.4kB] Get:2 http://archive.ubuntu.com/ubuntu/ maverick/main libpkcs11-helper1 i386 1.07-1build1 [43.8kB] Get:3 http://archive.ubuntu.com/ubuntu/ maverick/main openvpn-blacklist all 0.4 [1068kB] Get:4 http://archive.ubuntu.com/ubuntu/ maverick/main openvpn i386 2.1.0-3ubuntu1 [425kB] Fetched 1601kB in 2s (638kB/s) Preconfiguring packages ... Selecting previously deselected package liblzo2-2. (Reading database ... 27146 files and directories currently installed.) Unpacking liblzo2-2 (from .../liblzo2-2_2.03-2_i386.deb) ... Selecting previously deselected package libpkcs11-helper1. Unpacking libpkcs11-helper1 (from .../libpkcs11-helper1_1.07-1build1_i386.deb) ... Selecting previously deselected package openvpn-blacklist. Unpacking openvpn-blacklist (from .../openvpn-blacklist_0.4_all.deb) ... Selecting previously deselected package openvpn. Unpacking openvpn (from .../openvpn_2.1.0-3ubuntu1_i386.deb) ... Setting up liblzo2-2 (2.03-2) ... Setting up libpkcs11-helper1 (1.07-1build1) ... Setting up openvpn-blacklist (0.4) ... Setting up openvpn (2.1.0-3ubuntu1) ... * Restarting virtual private network daemon(s)... * No VPN is running. Processing triggers for libc-bin ... ldconfig deferred processing now taking place
配置 openvpn
在 Putty 执行依次逐行如下命令,遇到(y/n)的提示输入 y 回车,否则直接回车继续:gunzip -c /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz > /etc/openvpn/server.conf cp -r /usr/share/doc/openvpn/examples/easy-rsa/ /etc/openvpn/ cd /etc/openvpn/easy-rsa/2.0/ source vars ./clean-all ./build-ca ./build-key-server server ./build-key client ./build-dh执行上面的命令过程如下所示:
root@241541:/etc/openvpn# gunzip -c /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz > /etc/openvpn/server.conf root@241541:/etc/openvpn# cp -r /usr/share/doc/openvpn/examples/easy-rsa/ /etc/openvpn/ root@241541:/etc/openvpn# cd /etc/openvpn/easy-rsa/2.0/ root@241541:/etc/openvpn/easy-rsa/2.0# source vars NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/2.0/keys root@241541:/etc/openvpn/easy-rsa/2.0# ./clean-all root@241541:/etc/openvpn/easy-rsa/2.0# ./build-ca Generating a 1024 bit RSA private key .++++++ ........++++++ writing new private key to 'ca.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: State or Province Name (full name) [CA]: Locality Name (eg, city) [SanFrancisco]: Organization Name (eg, company) [Fort-Funston]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) [Fort-Funston CA]: Name []: Email Address [me@myhost.mydomain]: root@241541:/etc/openvpn/easy-rsa/2.0# ./build-key-server server Generating a 1024 bit RSA private key ......++++++ ............++++++ writing new private key to 'server.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: State or Province Name (full name) [CA]: Locality Name (eg, city) [SanFrancisco]: Organization Name (eg, company) [Fort-Funston]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) [server]: Name []: Email Address [me@myhost.mydomain]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/openvpn/easy-rsa/2.0/openssl.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'US' stateOrProvinceName :PRINTABLE:'CA' localityName :PRINTABLE:'SanFrancisco' organizationName :PRINTABLE:'Fort-Funston' commonName :PRINTABLE:'server' emailAddress :IA5STRING:'me@myhost.mydomain' Certificate is to be certified until Jul 28 09:21:30 2022 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated root@241541:/etc/openvpn/easy-rsa/2.0# ./build-key client Generating a 1024 bit RSA private key ..............++++++ .......................++++++ writing new private key to 'client.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: State or Province Name (full name) [CA]: Locality Name (eg, city) [SanFrancisco]: Organization Name (eg, company) [Fort-Funston]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) [client]: Name []: Email Address [me@myhost.mydomain]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/openvpn/easy-rsa/2.0/openssl.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'US' stateOrProvinceName :PRINTABLE:'CA' localityName :PRINTABLE:'SanFrancisco' organizationName :PRINTABLE:'Fort-Funston' commonName :PRINTABLE:'client' emailAddress :IA5STRING:'me@myhost.mydomain' Certificate is to be certified until Jul 28 09:22:53 2022 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated root@241541:/etc/openvpn/easy-rsa/2.0# ./build-dh Generating DH parameters, 1024 bit long safe prime, generator 2 This is going to take a long time ...............+..........................................................................+.............+.....................+.....................................+.................................... ............................................................................+.........................................................+...................................................................... ..................................................+........................................................................................................................................................... ...........................+...................................................+.......................................................................................................................+.... ..........................................+.......................................+.......................................................................................................................... ...........................................................+............................................................................................+.................................................... .+.............+......................+.............................................................+..+.....................+....................................................................+.... ...........................+..+..+.....+...+...............++*++*++*将刚才创建的文件复制到配置目录,继续执行如下命令:
cd /etc/openvpn cp /etc/openvpn/easy-rsa/2.0/keys/ca.crt . cp /etc/openvpn/easy-rsa/2.0/keys/server.crt . cp /etc/openvpn/easy-rsa/2.0/keys/server.key . cp /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem .执行结果如下:
root@241541:/etc/openvpn/easy-rsa/2.0# cd /etc/openvpn root@241541:/etc/openvpn# cp /etc/openvpn/easy-rsa/2.0/keys/ca.crt . root@241541:/etc/openvpn# cp /etc/openvpn/easy-rsa/2.0/keys/server.crt . root@241541:/etc/openvpn# cp /etc/openvpn/easy-rsa/2.0/keys/server.key . root@241541:/etc/openvpn# cp /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem .为了更方便的使用openvpn,这里我们需要修改openvpn的协议和端口,我们将通讯协议改为 tcp,端口改为 https 的端口号 443。 继续在 putty 里面执行如下命令:
sed -i 's/port.*/port 443/' /etc/openvpn/server.conf sed -i 's/;proto tcp.*/proto tcp/' /etc/openvpn/server.conf sed -i 's/.*proto udp.*/;proto udp/' /etc/openvpn/server.conf sed -i 's/;push "dhcp-option DNS 208.67.222.222"/push "dhcp-option DNS 208.67.222.222"/' /etc/openvpn/server.conf sed -i 's/;push "dhcp-option DNS 208.67.220.220"/push "dhcp-option DNS 208.67.222.220"/' /etc/openvpn/server.conf sed -i 's/keepalive 10 120/keepalive 1000 12000/' /etc/openvpn/server.conf sed -i 's/;push "redirect-gateway.*/push "redirect-gateway def1 bypass-dhcp"/' /etc/openvpn/server.conf执行结果如下所示:
root@241541:/etc/openvpn# sed -i 's/port.*/port 443/' /etc/openvpn/server.conf root@241541:/etc/openvpn# sed -i 's/;proto tcp.*/proto tcp/' /etc/openvpn/server.conf root@241541:/etc/openvpn# sed -i 's/.*proto udp.*/;proto udp/' /etc/openvpn/server.conf root@241541:/etc/openvpn# sed -i 's/;push "dhcp-option DNS 208.67.222.222"/push "dhcp-option DNS 208.67.222.222"/' /etc/openvpn/server.conf root@241541:/etc/openvpn# sed -i 's/;push "dhcp-option DNS 208.67.220.220"/push "dhcp-option DNS 208.67.222.220"/' /etc/openvpn/server.conf root@241541:/etc/openvpn# sed -i 's/keepalive 10 120/keepalive 1000 12000/' /etc/openvpn/server.conf root@241541:/etc/openvpn# sed -i 's/;push "redirect-gateway.*/push "redirect-gateway def1 bypass-dhcp"/' /etc/openvpn/server.conf配置完成,执行如下命令重启 openvpn :
/etc/init.d/openvpn restart执行结果如下:
root@241541:/etc/openvpn# /etc/init.d/openvpn restart * Stopping virtual private network daemon(s)... * Stopping VPN 'server' [ OK ] * Starting virtual private network daemon(s)... * Autostarting VPN 'server' [ OK ]
配置 防火墙
在Putty里面执行如下命令: 打开 IP 转发:echo 'net.ipv4.ip_forward=1' >> /etc/sysctl.conf sysctl -p继续执行如下命令,配置防火墙:
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o venet0 -j SNAT --to-source `ifconfig venet0:0|grep inet|awk '{print $2}'|awk -F: '{print $2}'`
iptables-save > /etc/iptables-rules
echo '#!/bin/sh' > /etc/network/if-up.d/iptablesload
echo 'iptables-restore < /etc/iptables-rules' >> /etc/network/if-up.d/iptablesload
echo 'exit 0' >> /etc/network/if-up.d/iptablesload
chmod +x /etc/network/if-up.d/iptablesload
大功告成,可以使用 OPEN VPN 了。
配置客户端
1 安装 openvpn 客户端 请点击 openvpn 2.2 打开后下载并安装。 2 复制配置文件 将安装目录的 sample-config 目录下面的 client.ovpn 复制到 安装目录下的 config 目录 如将 C:\Program Files\OpenVPN\sample-config\client.ovpn 复制到 C:\Program Files\OpenVPN\config 目录 3 修改 client.ovpn 配置文件 不要直接使用windows的记事本修改,请使用例如 Notepad++ 或 UltraEdit 等编辑器编辑 修改传输协议,注意请使用半角编辑,即关闭输入法进行编辑。 找到;proto tcp的行,删除前面的 ; 号,修改为
proto tcp找到
proto udp行,在前面加上 ; 号,修改为
;proto udp修改,需要连接的远程地址和端口: 找到
remote my-server-1 1194行,修改为:
remote 你的VPS的IP 443例如,(不可以照抄,需要将 184.82.9.30 改为你自己的VPS的地址):
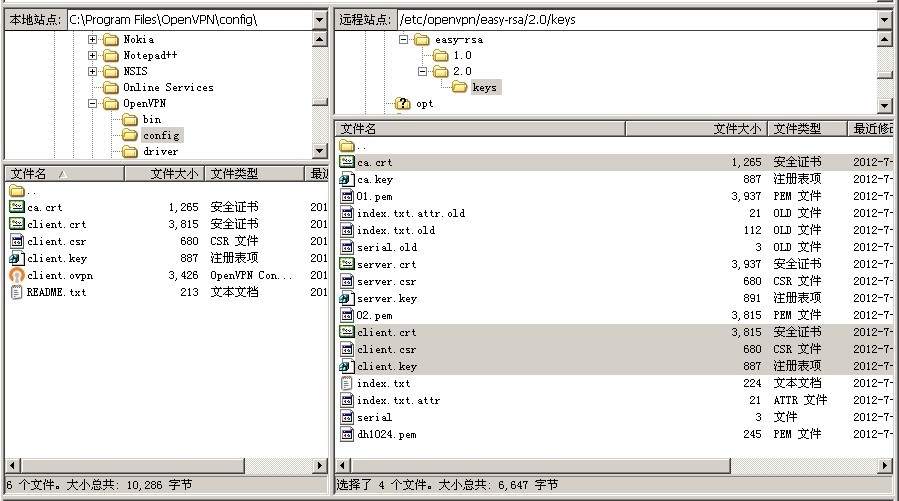
remote 184.82.9.30 4434 下载客户端证书文件 使用 filezilla 连接到服务器,到 /etc/openvpn/easy-rsa/2.0/keys 目录,将服务器的 ca.crt client.crt client.csr client.key 下载到 本地 openvpn 安装目录下的 config 目录,如下图所示:
 5 运行菜单里面的 OpenVPN GUI,出现在系统右下角,点击红色网络图标,右键 选择 connect 点击,图标变为绿色,即连接上。
5 运行菜单里面的 OpenVPN GUI,出现在系统右下角,点击红色网络图标,右键 选择 connect 点击,图标变为绿色,即连接上。
正文到此结束
- 本文标签: OpenVZ VPS
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二
热门推荐
相关文章
Loading...









![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

